📦 Cyber Security Word of the Week: Data Exfiltration! 📦
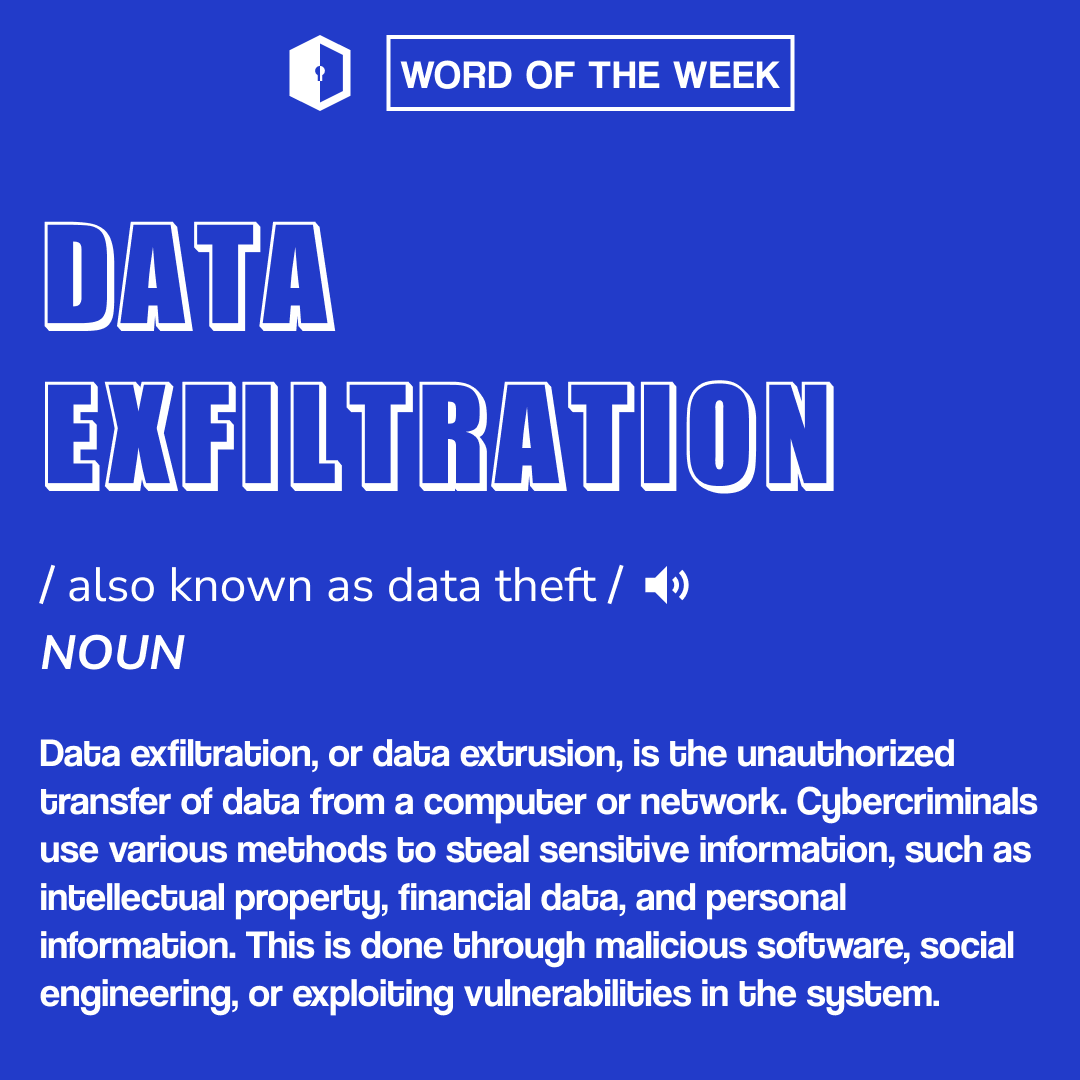
Data exfiltration, also known as data theft or data extrusion, is the unauthorized transfer of data from a computer or network. Cybercriminals use various methods to steal sensitive information, such as intellectual property, financial data, and personal information.
A giant company suffered a major data exfiltration resulting in the theft of 40 million credit and debit card records. 😱
Hackers infiltrated the company's network via a third-party vendor, leading to financial losses, reputational damage, and costly legal settlements. This incident highlights the importance of robust data protection measures and continuous monitoring.
🛡️ What is Data Exfiltration?
Data exfiltration, also known as data theft or data extrusion, is the unauthorized transfer of data from a computer or network. Cybercriminals use various methods to steal sensitive information, such as intellectual property, financial data, and personal information. This can be done through malicious software, social engineering, or exploiting vulnerabilities in the system.
🚨 Why is Data Exfiltration Critical?
Data exfiltration is critical because it can lead to severe consequences, including financial loss, reputational damage, and legal repercussions. Once sensitive data is stolen, it can be sold on the dark web, used for identity theft, or exploited for competitive advantage. Organizations must prioritize preventing data exfiltration to safeguard their assets and maintain trust with customers and stakeholders.
🛡️ How to Stay Safe from Data Exfiltration?
- Implement Strong Access Controls: Restrict access to sensitive data based on roles and responsibilities.
- Encrypt Sensitive Data: Use encryption to protect data both at rest and in transit.
- Monitor Network Traffic: Monitor network traffic for unusual activity indicating data exfiltration.
- Use Data Loss Prevention (DLP) Tools: Deploy DLP solutions to detect and prevent unauthorized data transfers.
- Conduct Regular Security Audits: Perform regular audits and vulnerability assessments to identify and mitigate potential weaknesses.
"Guard your valuable data against theft. Implement strong security measures and stay vigilant. Together, we can prevent data exfiltration!"
Let’s strengthen our defences and ensure our data remains secure.
Stay tuned for more insights and tips in our Cyber Security Word of the Week series! 🌐🔒

