⌨️ Cyber Security Word of the Week: Keylogger! ⌨️
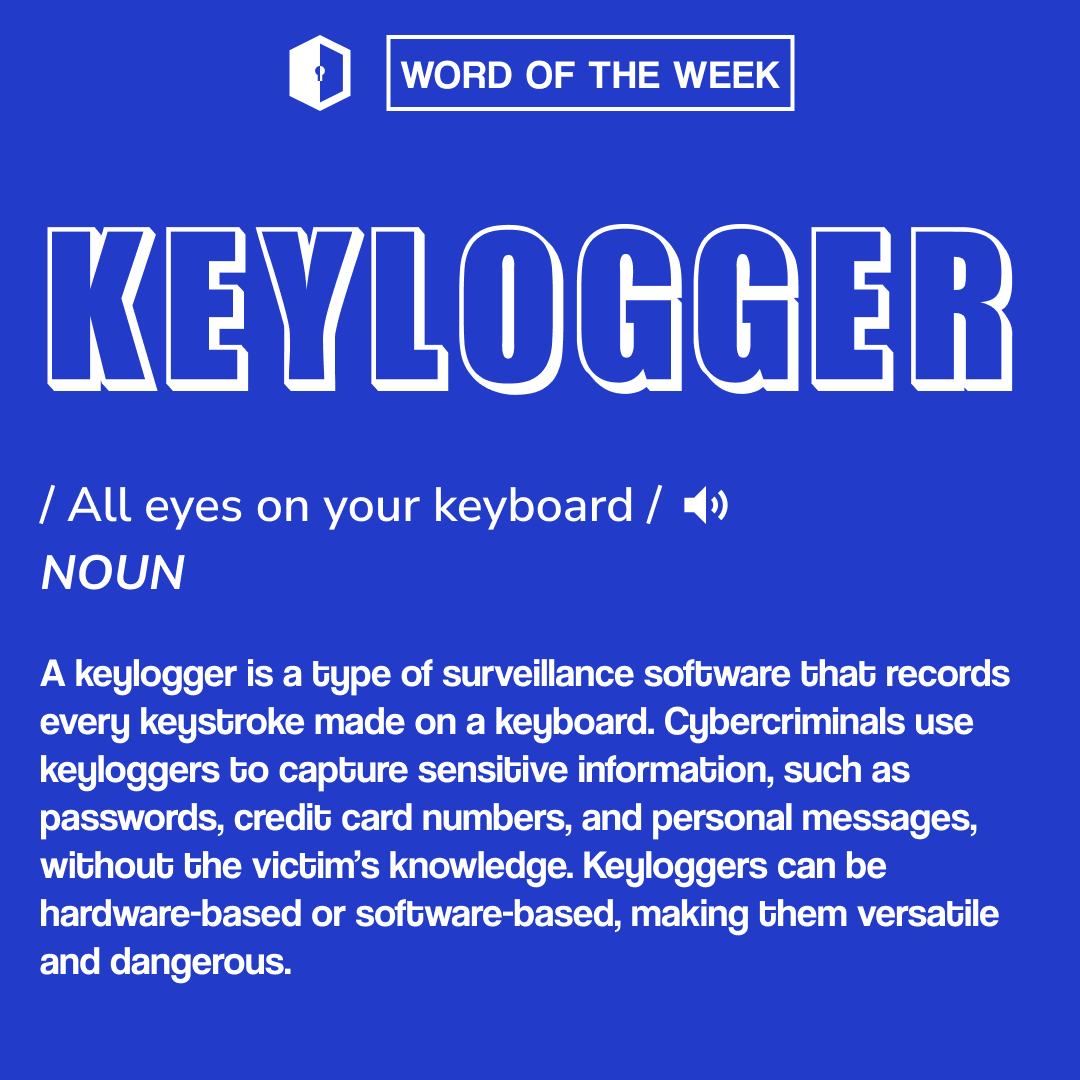
A keylogger is a type of surveillance software that records every keystroke made on a keyboard. Cybercriminals use keyloggers to capture sensitive information, such as passwords, credit card numbers, and personal messages, without the victim’s knowledge.
A major financial institution discovered a keylogger on an employee’s computer!!
The keylogger had captured login credentials and other sensitive information for months, leading to unauthorized access and significant data breaches. This incident highlights the importance of robust cybersecurity measures and regular monitoring.
🖥️ What is a Keylogger?
A keylogger is a type of surveillance software that records every keystroke made on a keyboard. Cybercriminals use keyloggers to capture sensitive information, such as passwords, credit card numbers, and personal messages, without the victim’s knowledge. Keyloggers can be hardware-based or software-based, making them versatile and dangerous.
🚨 Why is a Keylogger Critical?
Keyloggers are critical because they can silently steal vast amounts of sensitive data, leading to identity theft, financial fraud, and privacy breaches. Since they operate undetected, victims often remain unaware of the compromise until significant damage has been done. Keyloggers can be installed through malicious email attachments, software downloads, or physical devices.
🛡️ How to Stay Safe from Keyloggers?
- Use Antivirus Software: Install and regularly update antivirus software that can detect and remove keyloggers.
- Enable Two-Factor Authentication: Implement 2FA for an added layer of security, making it harder for cybercriminals to misuse captured credentials.
- Be Cautious with Downloads: Only download software from trusted sources and avoid clicking on suspicious links or email attachments.
- Regularly Update Software: Keep your operating system and software up to date with the latest security patches.
- Use a Virtual Keyboard: For highly sensitive entries, consider using a virtual keyboard to bypass hardware keyloggers.
"Secure your keys, protect your data. Let’s stay vigilant and prevent keyloggers from stealing our information!"
Let’s enhance our defenses and keep our data safe from prying eyes.
Stay tuned for more insights and tips in our Cyber Security Word of the Week series! 🌐🔒

